A: A computer network exists when one machine can pass data to another machine.
Q: Why network computers?
A: To allow data to be transferred from one computer to one or more other computer(s). (This can include printers, fax machines and other less obvious computers.)
Q: What is the most important thing to know about a computer network?
A: To separate your private data from your public data PRIOR to making a network connection. The private data should never be stored on a computer that has a wire leading to the Internet. (This means: if private data is to be stored digitally, it should not be stored on a device with any wire or wireless connection. No modem. No PC Anywhere. No internet connection. No wireless connections nor antennas. No etc.
Then, determine how to maximize efficiency and minimize risk when moving and storing your data.
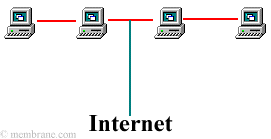
Following are examples of three computer networks:

In this example, the computers are networked together with ethernet connections. The ethernet is then connected to the Internet through either a modem, hub, switch, router (or a variety of other highspeed Internet connectors.)
Once the internet connection has been made, It is prudent to assume that these computers have been compromised. Therefore, these computers should be used only for public information. In addition, extra measures should be taken to prevent their destruction and/or illegal use by a third-party.
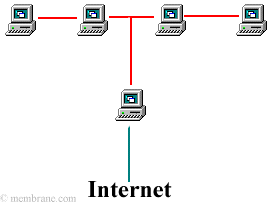
In this example, the computers are networked together with ethernet connections. The ethernet is then connected to a firewall. The firewall is then connected to the Internet through either a modem, hub, switch, router (or a variety of other highspeed Internet connectors.)
This is often the most costly networking method. So, have you asked yourself:
Why are we moving/storing the data in this way?
And, who is responsible for securing the data?
The "who" is very, very important. Monitoring a firewall is a 24-hour / 7-day-a-week job that must be performed by humans. There is no "off-the-shelf" remedy. Security hardware (such as hubs, switches, routers, etc.) and security software are only as good as the humans responsible for maintaining their security. Also important to note: collecting email, viewing webpages, etc. are ways of bringing unauthorized data behind your firewall. Once malicious data has touched any one network computer, all of the other networked computers should be considered compromised.
If the reason for moving or storing the data this way is compelling enough to proceed, then -- WHO?
Eventually, networks connected to the Internet will be compromised. Thus, a crisis management plan that includes on-site and off-site backups is essential. Who will create and protect these backups?
Who will be responsible for the security? What are the names of the individuals? You should be able to name the humans responsible and understand the scenarios for executing your crisis management plan.
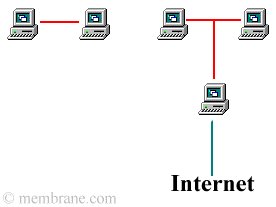
In this example, computers are first separated into "private" and "public." Then, the private computers are networked together with ethernet connections.
The public computers are also networked with ethernet. Then, they are connected to the Internet through either of the above mentioned methods.
Decentralizing your public and private data is often the most financially prudent computer networking plan.
Back To: Studies in Computer & Internet Security